More on WebDAV - Connecting a remote WebDAV folder in Windows
After some failed attempt at this, I think I found the right way to "mount" a remote WebDAV folder under Windows' Explorer.
Initially my baby steps took me here: https://note.woodpeckersnest.space/share/0TJT81fgI8Jy
After following that tutorial I didn't succeed, so I investigated further. I can say that everythig looks correct until you get to point 9.
The address they tell you have to enter isn't correct in my experience and they aren't even using https for the URL. What worked for me was instead something like:
\\webdav.woodpeckersnest.space@SSL\folder
You have to input the network-path-stile address which is common in Windows, as in: double backslash, FQDN of your WebDAV server, "@SSL" and then the path (folder) where you have access to files in your WebDAV server, with a backslash preceding it.
That's it, a prompt will ask for username and password and then a new Network Path (WebFolder) will be connected in Explorer, just below your local drives.
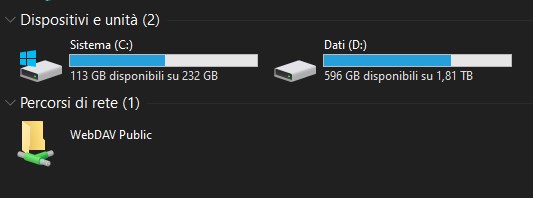
You can then browse, copy, upload, delete (and so on) whatever content you like.
EDIT: Just found out I couldn't rename files/folders from Windows or Total Commander (Android)
Fixed by setting nginx virtualhost like this:
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name webdav.woodpeckersnest.space;
# HTTPS configuration
ssl_certificate /etc/letsencrypt/live/webdav.woodpeckersnest.space/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/webdav.woodpeckersnest.space/privkey.pem;
access_log /var/log/nginx/webdav/access.log;
error_log /var/log/nginx/webdav/error.log;
location / {
set $destination $http_destination;
if ($destination ~* ^https(.+)$) {
set $destination http$1;
}
proxy_set_header Destination $destination;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Host $host;
proxy_pass http://127.0.0.1:17062/;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
}
client_max_body_size 0;
}
Now I'm quite happy 😀