These days I am tinkering with a Mailing List for Delta Chat powered by mlmmj
I was able to create the list and set up Postfix correctly - instructions are quite clear even if on a couple settings I had to do some troubleshooting looking at logs.. Now I have this Mailing List called deltachat@woodpeckersnest.eu which you can subscribe to by sending an email to deltachat+subscribe@woodpeckersnest.eu and following further instructions.
Initially Delta Chat would create groups of people with the ML's address inside of it, thus splitting every conversation by users participating in it. This was later fixed by adding the following lines in list-dir/control/customheaders file:
X-Mailinglist: deltachat
Reply-To: deltachat@woodpeckersnest.space
List-ID: DC Mailing List <deltachat.woodpeckersnest.eu>
List-Post: <mailto:deltachat@woodpeckersnest.eu>
Now a proper Super Group is created and everyone¹ is able to message in it.
¹ Well, not actually everyone since a member still has issues but I'm positive that can be fixed by chatting again with the ML's address and removing all weird groups created earlier.

This ^ is how the supergroup looks in my chat window - the avatar is only local, it can't be set for every member but the name is the same for everyone.
Then someone "complained" for the lack of anonymity for users email addresses, like it's done in the "official" Delta Chat's MLs.. So I asked on codeberg but it seems to be a missing feature (I'm still waiting for replies 😬).
This is it for now, will keep you posted when/if I have news.
Thanks to Zash and Jcbrand in the "Converse" MUC and a bit of hacking I was able to set up a few community plugins for my conversejs install as a prosody module.
Here's the configuration in /etc/prosody/prosody.cfg.lua:
conversejs_resources = "/usr/local/lib/prosody/modules/mod_conversejs/dist"
conversejs_tags = {
-- Load favicon
[[<link rel="shortcut icon" href="https://woodpeckersnest.space/images/converse-js.ico">]];
-- Load libsignal-protocol.js for OMEMO support (GPLv3; be aware of licence implications)
[[<script src="https://cdn.conversejs.org/3rdparty/libsignal-protocol.min.js"></script>]];
-- Load community plugins
[[<link type="text/css" rel="stylesheet" media="screen" href="conversejs/dist/plugins/search/search.css" />]];
[[<script src="conversejs/dist/plugins/actions/actions.js"></script>]];
[[<script src="conversejs/dist/plugins/search/search.js"></script>]];
[[<script src="conversejs/dist/plugins/search/jspdf.debug.js"></script>]];
[[<script src="conversejs/dist/plugins/search/jspdf.plugin.autotable.js"></script>]];
[[<script src="conversejs/dist/plugins/toolbar-utilities/toolbar-utilities.js"></script>]];
[[<script src="conversejs/dist/plugins/screencast/screencast.js"></script>]];
}
conversejs_options = {
locked_domain = "woodpeckersnest.space";
auto_focus = true;
view_mode = "fullscreen";
allow_registration = false;
auto_reconnect = true;
reuse_scram_keys = true;
muc_clear_messages_on_leave = true;
clear_cache_on_logout = false;
play_sounds = true;
whitelisted_plugins = {"actions", "search", "toolbar-utilities", "screencast"};
}
You'll have to copy the plugins directories (actions, search etc..) in this path:
/usr/local/lib/prosody/modules/mod_conversejs/dist/plugins/
Then reload configuration and conversejs module or restart prosody.
Already found a bug in "toolbar-utilities" and haven't still had a chance to try the screencast plugin, but they look good for the most part.
Maybe I will add Jitsi Meet or Voice Chat at some point.. Not now though. ¹
EDIT: screencast is working alright, but not in the way you'd expect it. It's not a live streaming, instead it's a recording of your screen which gets uploaded once you stop the cast.. I wouldn't say it's perfect but not even bad.
¹ I've added them 😛

Little OT, but not so much 😀
To manage your sieve scripts from Thunderbird 115 there's this nightly build, until developer will code a proper release with fixes.
You can read the issue at https://github.com/thsmi/sieve/issues/893 and I've uploaded the file for convenience here.
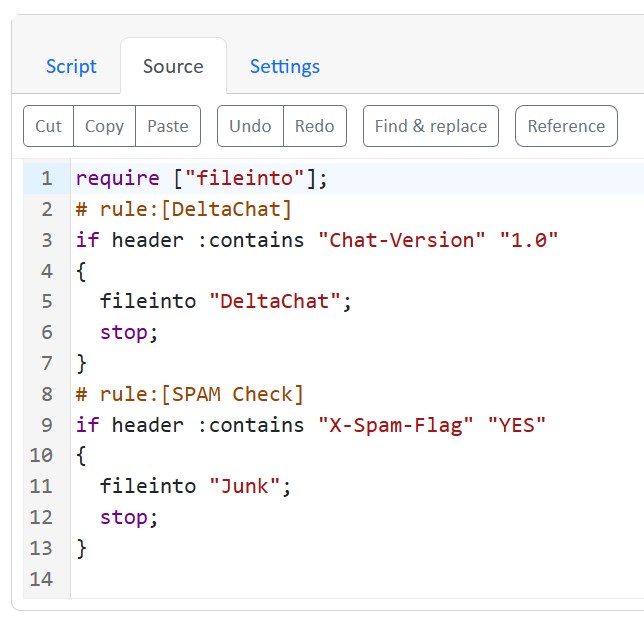
My server comes with a default sieve to filter spam messages and another one to move Delta Chat emails:
require ["fileinto"];
# rule:[DeltaChat]
if header :contains "Chat-Version" "1.0"
{
fileinto "DeltaChat";
stop;
}
# rule:[SPAM Check]
if header :contains "X-Spam-Flag" "YES"
{
fileinto "Junk";
stop;
}
Remember: don't ever use special characters in your DB's users password!!
I have been troubleshooting a migration from mariadbd to pgsql for several hours, until I tried changing my password, which, weirdly enough, was working to connect roundcube but gave errors with pgloader. Once I successfully migrated using the same password with those special characters, roundcube wouldn't connect with pgsql, so I made another fighting round! Finally changed my pgsql password to some letters and numbers only and BAM!, it worked.
Then I stopped mariadbd and disabled the service; now I have more than 200MB RAM freed¹.
¹ See previous post.
I'm still struggling to understand why mariadbd uses so much memory for just 1 DB and 1 application, which in this case is roundcube.
I tried changing this value to no avail.. If anyone wants to share some thoughts I would appreciate:
[mariadb]
innodb_buffer_pool_size=128M
Leave a comment if you know shit. Thanks
EDIT: some details
OVH VPS, 1 core, 2GB, 20 GB SSD. mariadb-server 1:10.11.4-1~deb12u1. roundcube DB size 2.41MB, 17 tables. RAM taken at process restart 240MB.
I was enabling Exim on my IONOS VPS to deliver email through a smarthost and encountered the error message in this post's title (unable to send to Gmail users.. It's always them!)
After fiddling a while with DMARK and SPF I reconfigured Exim itself to rewrite sender address, so that emails coming from "spacenest.it" (IONOS domain) were sent as coming from "woodpeckersnest.eu", the smarthost and real email server.
Everything is done via this command:
# dpkg-reconfigure exim4-config
And the resulting configuration in /etc/exim4/update-exim4.conf is:
dc_eximconfig_configtype='smarthost'
dc_other_hostnames='cassandra.spacenest.it;spacenest.it'
dc_local_interfaces='127.0.0.1'
dc_readhost='woodpeckersnest.eu'
dc_relay_domains=''
dc_minimaldns='false'
dc_relay_nets=''
dc_smarthost='pandora.woodpeckersnest.space::587'
CFILEMODE='644'
dc_use_split_config='false'
dc_hide_mailname='true'
dc_mailname_in_oh='true'
dc_localdelivery='mail_spool'
On OVH's postfix I just had to modify this line in /etc/postfix/main.cf:
mynetworks = 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128 94.143.138.27/32
where that last IP is the IP Address of my IONOS server.
I had previously discussed this issue on XMPP and on my Schleuder Mailing List, but there's news.
My ".space" domain is blacklisted by Google and others top email services because it is considered spammy - I still don't understand how you can blacklist a whole tld for spam but that's how it goes..
So I purchased a new ".eu" domain and set it up as virtual host in postfix.. But I was still using a third party relay to deliver emails to Gmail, Hotmail and iCloud. This relay works with "credits", each email you send using their free service is equal to 1 credit and you get 1000 credits per month (BIG Thanks to Kévin from Delta Chat for helping me out with this).
Now, I haven't ever reached the maximum allowed quota but I felt like removing the casters at least for Gmail, since this .eu domain should do the job just fine and because I cannot actually remove Hotmail, since they have my server IP banned for whatever reason.
So, I removed the gmail line in my transport file for postfix, ran postmap and reloaded postfix.service. Finally I sent a Ping over to "Delta Chat Italian Offtopic Group" where there are 2 people with gmail accounts and everything was fine, no email returned back to sender.
I'll keep going like this until problems!!
Now, if anyone is interested on how my transport file looks like, I'll share 😀
outlook.com smtp:[outbound.mailhop.org]:587
hotmail.com smtp:[outbound.mailhop.org]:587
outlook.fr smtp:[outbound.mailhop.org]:587
hotmail.it smtp:[outbound.mailhop.org]:587
mail.icloud.com smtp:[outbound.mailhop.org]:587
* :
You need an account on DuoCircle and you need to authenticate yourself (in postfix) for their smtp to accept emails from your server.
I'm not very familiar with javascript when it come to websites - a bit better is node.js, but that's another story..
I just wanted to give credit to my Steam friend andrei-kom (Thanks Andrei) for this piece of javascript he wrote to enhance the side menu of my main website. Now the buttons are highlighted not just on press but also when scrolling the page up and down! Woo-hoo 😀
Here's the code:
$(document).ready(function () {
$('a').on('click', function (e) {
$('a').removeClass('w3-hover-black-activated');
$(this).addClass('w3-hover-black-activated');
});
$('#home').addClass('contentBlock');
$('.w3-content').addClass('contentBlock');
$(window).scroll(function () {
var pageOffset = window.pageYOffset + 64;
$('.contentBlock').each(function () {
var contentBlockOffset = $(this).offset().top;
var id = $(this).attr('id');
if (id == 'home') {
id = '';
}
if (pageOffset >= contentBlockOffset) {
$('a.w3-button').removeClass('w3-hover-black-activated');
$('a.w3-button[href="#' + id + '"]').addClass('w3-hover-black-activated');
}
});
});
});
wg0.conf
[Interface]
# specify generated private key for server
PrivateKey = <privkey>
# IP address for VPN interface
Address = 172.16.100.1/32
MTU = 1420
# UDP port WireGuard server listens
ListenPort = 51820
# set routing rules like follows to access to local network via VPN session
PostUp = iptables -A FORWARD -i wg0 -j ACCEPT; iptables -t nat -A POSTROUTING -o ens3 -j MASQUERADE
PostDown = iptables -D FORWARD -i wg0 -j ACCEPT; iptables -t nat -D POSTROUTING -o ens3 -j MASQUERADE
# change "ens3" with your interface
[Peer]
# specify public key for client
PublicKey = <pubkey>
# clients' VPN IP addresses you allow to connect
# possible to specify subnet ⇒ [172.16.100.0/24]
AllowedIPs = 172.16.100.6
client.conf
[Interface]
# Private IP Address
Address = 172.16.100.6/32
# Client's Private Key
PrivateKey = <privkey>
# Server's listening port
ListenPort = 51820
[Peer]
# Server's Public Key
PublicKey = <pubkey>
AllowedIPs = 0.0.0.0/0
# Server's IP:port
Endpoint = 51.195.43.203:51820
If you want to scan a QR code on your phone to load the client.conf, do as follows:
# apt install qrencode
$ qrencode -t utf8 < client.conf
A QR code will appear, scan it.
Thanks to "to_red" for helping me out with the configuration 😉
Using the Maildir mailbox format, emails are stored in under the recipient user’s home folder /home/<username>/Maildir.
# postconf -e 'home_mailbox = Maildir/'
You might also want to add the Maildir setup to the user home directory template so that it is automatically configured when a new user account is created:
# maildirmake.dovecot /etc/skel/Maildir
# maildirmake.dovecot /etc/skel/Maildir/.Drafts
# maildirmake.dovecot /etc/skel/Maildir/.Sent
# maildirmake.dovecot /etc/skel/Maildir/.Trash
# maildirmake.dovecot /etc/skel/Maildir/.Templates
The same Maildir can be added to the current user with the commands below. Replace the $USER with any existing username:
# cp -r /etc/skel/Maildir /home/$USER/
# chown -R $USER:$USER /home/$USER/Maildir
# chmod -R 700 /home/$USER/Maildir
# adduser $USER mail
Also create a “.muttrc” file under /etc/skel and copy paste this content in it:
set mbox_type=Maildir
set folder="~/Maildir"
set mask="!^\\.[^.]"
set mbox="~/Maildir"
set record="+.Sent"
set postponed="+.Drafts"
set spoolfile="~/Maildir"





